Let’s dive into the details of what a privacy risk assessment is, why it can benefit businesses, and how to conduct one. - dataprivacy datasecurity
, and others all require varying extents of personal information management, maintenance, and control. By conducting a privacy risk assessment, businesses can identify compliance gaps, evaluate gaps and their risks and treat them - before suffering from the legal and financial implications of non-compliance.
A privacy risk assessment is an opportunity for businesses - to do the right thing for both their customers and to protect their business - and reposition themselves as a privacy-first entity.
A data map can include information about the number of data sources, their type, the types of data they contain, data accuracy, data quality, data structure, who has access to the data source, and more.
United States Latest News, United States Headlines
Similar News:You can also read news stories similar to this one that we have collected from other news sources.
 Gerrit Cole Lets His Second ALDS Gem Do the TalkingIf there was a question of paternity between Gerrit Cole and the Guardians, the Yankees’ ace seems to have answered it stephapstein on Cole's season-saving performance
Gerrit Cole Lets His Second ALDS Gem Do the TalkingIf there was a question of paternity between Gerrit Cole and the Guardians, the Yankees’ ace seems to have answered it stephapstein on Cole's season-saving performance
Read more »
 All This Talk About “Quiet Quitting” Is AbsurdThis is the kind of thinking that lets employers take advantage of employees in the first place.
All This Talk About “Quiet Quitting” Is AbsurdThis is the kind of thinking that lets employers take advantage of employees in the first place.
Read more »
 A Beginner's Guide on Ransomware: How To Identify and Prevent Attacks | HackerNoonRansomware is a different kind of malware. Find out how to identify and prevent its attacks that encrypt your files and demand a paid ransome for data access. - by juxtathinka cybersecurity cybersecurityawareness
A Beginner's Guide on Ransomware: How To Identify and Prevent Attacks | HackerNoonRansomware is a different kind of malware. Find out how to identify and prevent its attacks that encrypt your files and demand a paid ransome for data access. - by juxtathinka cybersecurity cybersecurityawareness
Read more »
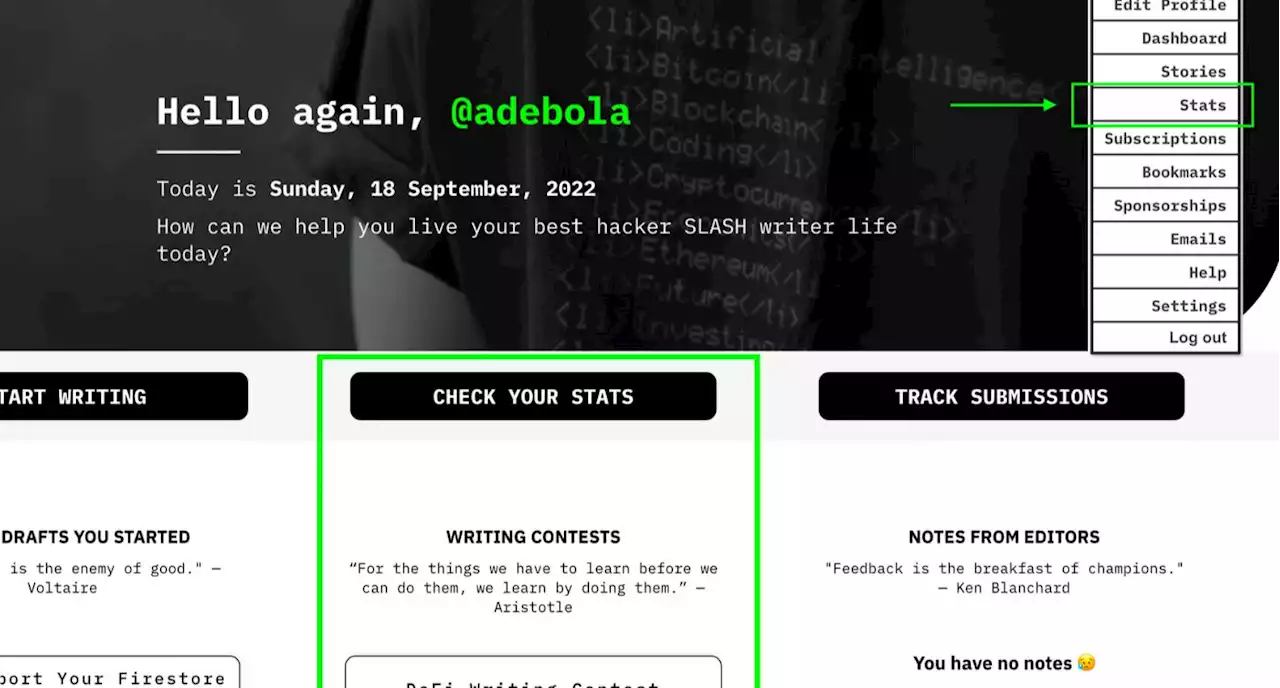 Introducing the Brand New Stats Page on HackerNoon | HackerNoonIn this blog, we’re going to take a quick look at all the stats we provide to writers on HackerNoon to help them supercharge their writing. - hackernoonproduct storystats
Introducing the Brand New Stats Page on HackerNoon | HackerNoonIn this blog, we’re going to take a quick look at all the stats we provide to writers on HackerNoon to help them supercharge their writing. - hackernoonproduct storystats
Read more »
 Gaussian Co-Ordinates | HackerNoonRelativity: The Special and General Theory by Albert Einstein is part of HackerNoon’s Book Blog Post series. - science physics
Gaussian Co-Ordinates | HackerNoonRelativity: The Special and General Theory by Albert Einstein is part of HackerNoon’s Book Blog Post series. - science physics
Read more »
