Learn how MASC uses generalizable mutation operators to detect crypto-API misuse, improving the robustness of crypto-detectors.
Authors: Amit Seal Ami, Computer Science Department, William & Mary Williamsburg, Virginia, USA, and this author contributed equally to this paper ; Syed Yusuf Ahmed, Institute for Information Technology, University of Dhaka Dhaka, Bangladesh, and this author contributed equally to this paper ; Radowan Mahmud Redoy, Institute for Information Technology, University of Dhaka Dhaka, Bangladesh, and this author contributed equally to this paper ; Nathan Cooper, Computer Science Department,...
Authors: Amit Seal Ami, Computer Science Department, William & Mary Williamsburg, Virginia, USA, and this author contributed equally to this paper ; Syed Yusuf Ahmed, Institute for Information Technology, University of Dhaka Dhaka, Bangladesh, and this author contributed equally to this paper ; Radowan Mahmud Redoy, Institute for Information Technology, University of Dhaka Dhaka, Bangladesh, and this author contributed equally to this paper ; Nathan Cooper, Computer Science Department,...
United States Latest News, United States Headlines
Similar News:You can also read news stories similar to this one that we have collected from other news sources.
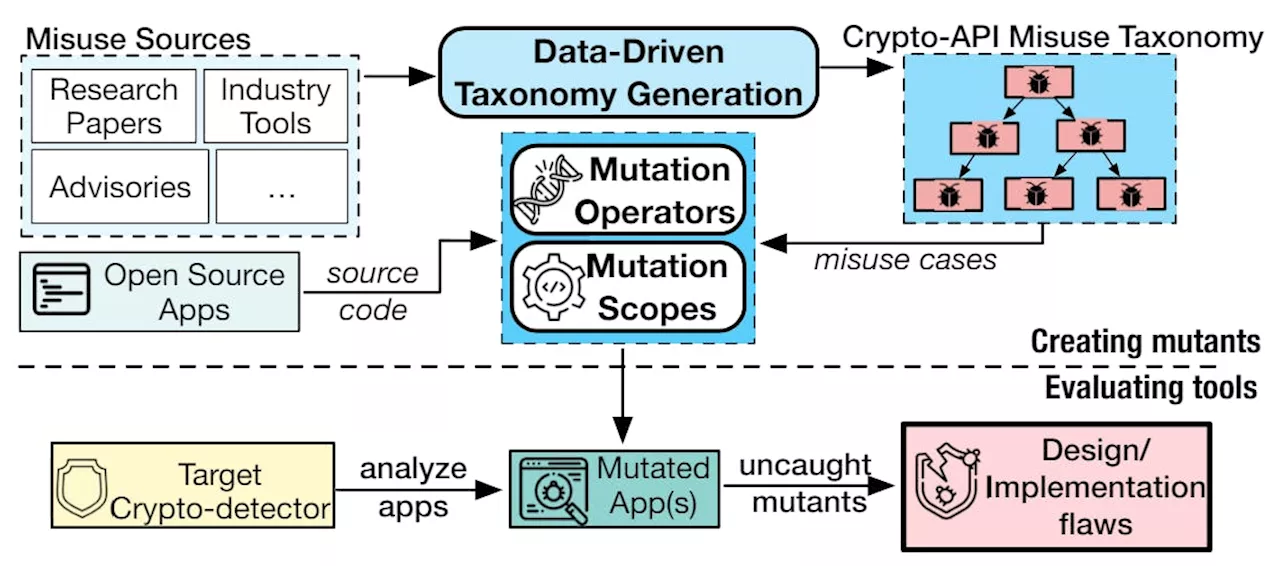 MASC: A Tool for Mutation-Based Evaluation of Static Crypto-API Misuse DetectorsLearn about MASC, an advanced tool designed for evaluating crypto-detectors, identifying crypto-API misuse, and enhancing software security.
MASC: A Tool for Mutation-Based Evaluation of Static Crypto-API Misuse DetectorsLearn about MASC, an advanced tool designed for evaluating crypto-detectors, identifying crypto-API misuse, and enhancing software security.
Read more »
 MASC's Three Mutation Scopes for Comprehensive Crypto-API Misuse AnalysisDiscover how MASC's Main, Similarity, and Exhaustive Scopes enhance the detection of crypto-API misuses in software development.
MASC's Three Mutation Scopes for Comprehensive Crypto-API Misuse AnalysisDiscover how MASC's Main, Similarity, and Exhaustive Scopes enhance the detection of crypto-API misuses in software development.
Read more »
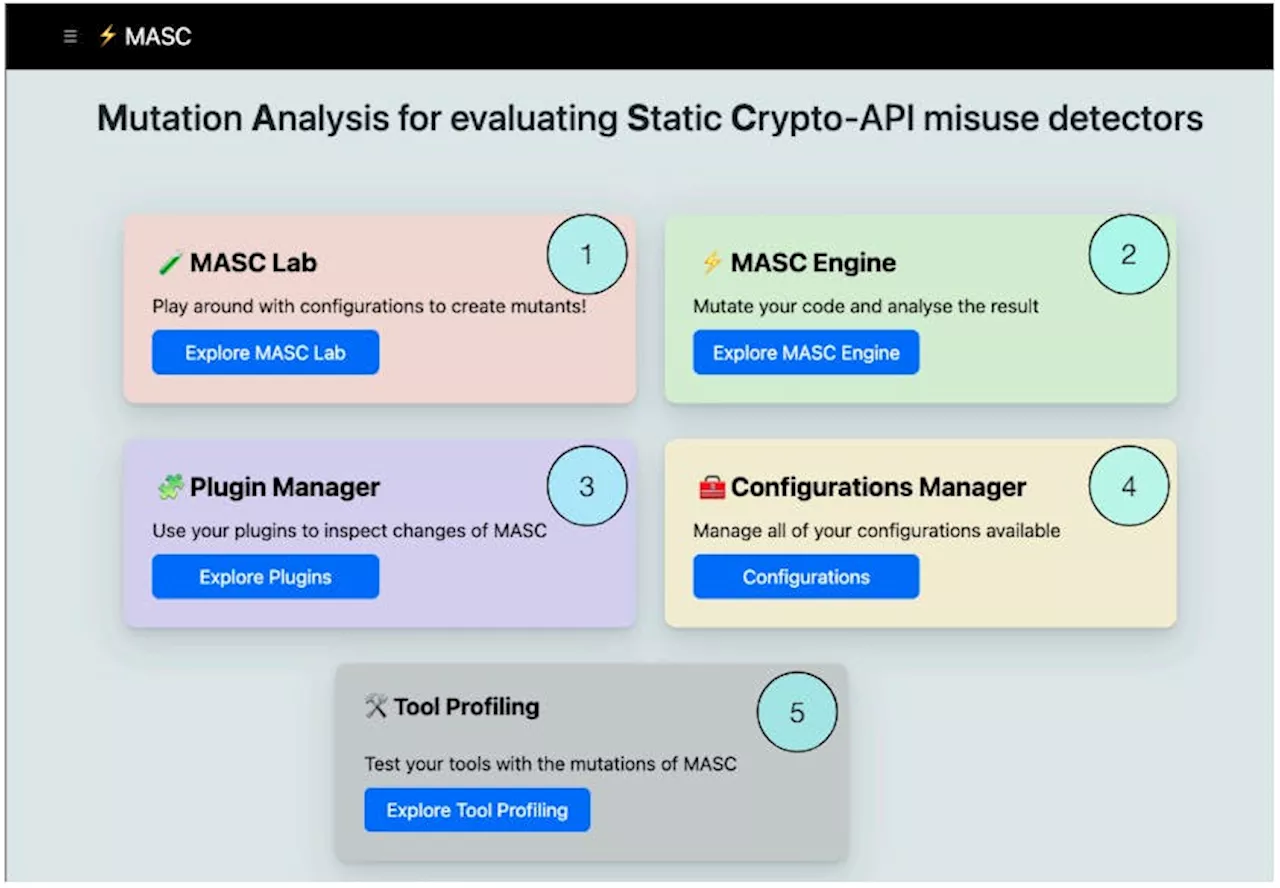 MASC User Guide: Experiment, Mutate, and Analyze Crypto-API MisusesLearn how to use MASC via command line and web interfaces for testing and analyzing crypto-API misuses in software development.
MASC User Guide: Experiment, Mutate, and Analyze Crypto-API MisusesLearn how to use MASC via command line and web interfaces for testing and analyzing crypto-API misuses in software development.
Read more »
 The Road Ahead for MASC: Expanding Crypto-API Misuse DetectionExplore the future enhancements and concluding insights of MASC, focusing on extending customization and evaluating additional crypto-detectors.
The Road Ahead for MASC: Expanding Crypto-API Misuse DetectionExplore the future enhancements and concluding insights of MASC, focusing on extending customization and evaluating additional crypto-detectors.
Read more »
 Planet Of The Apes' Simian Flu Explained: Origin, Effects & MutationRobert Pitman is a Movies/TV features writer for ScreenRant and loves all things nerdy. He has had experience with editing and SEO in his time working at WVUA 90.7 FM, the University of Alabama&039;s official student radio station.
Planet Of The Apes' Simian Flu Explained: Origin, Effects & MutationRobert Pitman is a Movies/TV features writer for ScreenRant and loves all things nerdy. He has had experience with editing and SEO in his time working at WVUA 90.7 FM, the University of Alabama&039;s official student radio station.
Read more »
FDA Chief Tells Senate Agency Is Preparing for Bird Flu MutationThe Food and Drug Administration (FDA) informed legislators on Wednesday that the agency is making preparatory measures in case the current avian flu is able to mutate and transmit to humans on a massive scale.
Read more »
