Apple is working on a fix to exterminate the iOS 15, iPadOS 15 Safari bug

A few days ago we told you about a rather serious Safari bug that could, in certain hands, lead to the theft of personal data. The report from FingerprintJS said that the bug "lets any website track your internet activity and even reveal your identity." The security research firm submitted the bug to the WebKit Bug Tracker on November 28, 2021, and according to MacRumors, a fix from Apple appears to be coming soon.
On GitHub, a WebKit commit indicates that Apple has its engineers working on a fix to exterminate the bug. This is expected to be disseminated shortly to iPhone, iPad, and Mac users via updates to iOS, iPadOS, and macOS Monterey respectively. WebKit is the web browser engine used by Safari and since Apple requires all browsers on the iPhone and iPad to be driven by WebKit, third-party browsers such as Chrome and Edge are afflicted with the same bug on iOS 15, and iPadOS 15.
Hackers can exploit this bug to obtain your Google User ID
The bug allows any website that uses the IndexedDB API for data storage to get the names of other websites opened by the user during a browsing session even if they are opened in a different tab or window. Affected sites also must use IndexedDB, which is known to hold "a significant amount of data."
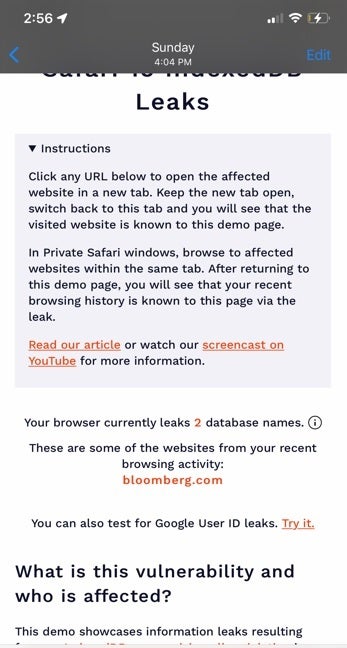
Demo shows how Safari bug can reveal the names of certain websites you've recently visited
Some of these databases will expose user-specific identifiers that can be used by attackers to capture the name of the user. Apps that place these user-specific identifiers in their databases include YouTube, Google Calendar, and Google Keep.
Identifiers used with apps like YouTube, Google Calendar and Google Keep include a person's Google User ID. You can prove this for yourself by opening Safarileaks.com on your iPhone or iPad's mobile web browser. Follow the directions and depending on what sites you've recently visited, your Google User ID will appear along with the name of certain websites that you've recently opened.
Devices running iOS 14 or iPadOS 14 are not affected by the bug
With your Google User ID, a hacker can identify a specific Google account. Perhaps a bit more concerning, in combination with Google APIs, the bug could reveal your profile picture to a hacker at the least and much more personal information in the worst-case scenario.
The bug does not impact Safari 14 on macOS, or the mobile browser on iOS 14, and iPadOS 14. However, with 72% of iPhone models released over the last four years and 63% of all compatible iPhone units running iOS 15, that works out to a large number of Apple handsets that can be exploited.
One of the problems with this bug is that it doesn't require that you do anything special to put yourself at risk. You don't need to be tricked into tapping a link or opening a certain website. And FingerprintJS discovered that 30 of the top 1,000 visited sites (computed by Alexa) have IndexedDB right on their home page which makes it easy for an iPhone or iPad user to step right into this bug unwittingly.
And until Apple delivers the update, there really isn't much that a user can do to avoid this. Mac users can switch browsers, but iOS and iPadOS users must stick with a browser that runs on the WebKit engine so that is not going to help much. One suggestion is to block all JavaScript by default and only allow it only on sites that are 100% trusted.
The WebKit Commit suggests that the update will be coming soon, but that might not be soon enough for privacy-focused iPhone and iPad users who aren't happy with the idea that their browsing history, profile picture, and more personal data can be discovered along with their identity.












Things that are NOT allowed: